Apteriks IPAM is a hosted service
Pre-configured, reliable, and frequently upgraded with new features
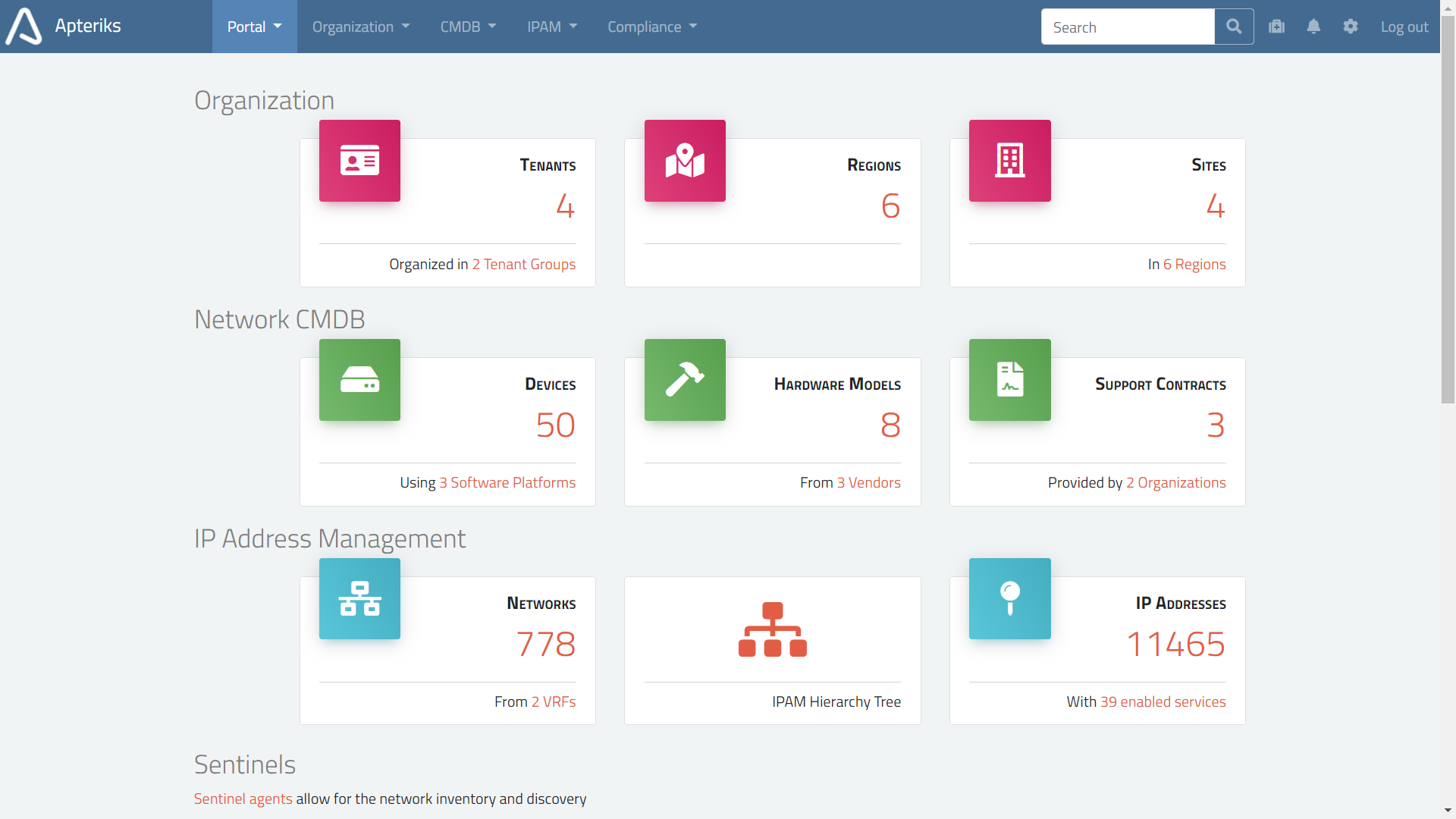
The IPAM helps you to plan and manage the assignment and use of IP addresses within your Organisation.
It takes only a minute to register and start using it.
Full integration with CMDB
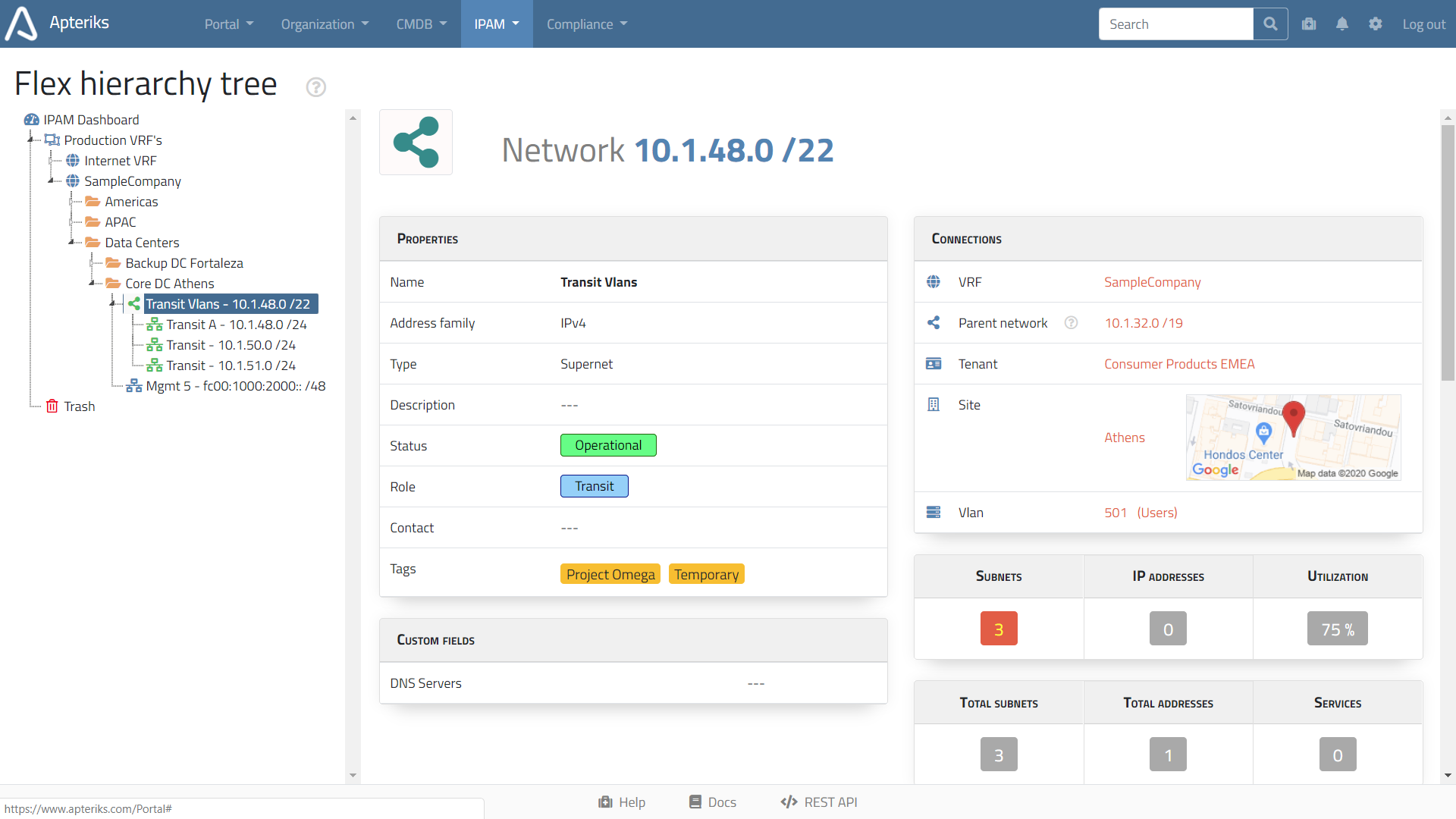
IPAM Vlans, Networks and IP addresses do not exist in isolation; they can be linked to your Organisational structure and assets captured in the Configuration Management Database.
-
Example:
An IPAM VRF can be linked to a Tenant (Business Unit or Department).
When you open a Tenant view, you will see all associated Sites, Devices, IP VRFs, Networks and IP addresses. -
Example:
An IP Network can be linked to a Department or Site.
When you open a Site view you will see all associated Vlans, Networks, Devices, and more.
Built-in network discovery engine
You can speed up or automate your network discovery
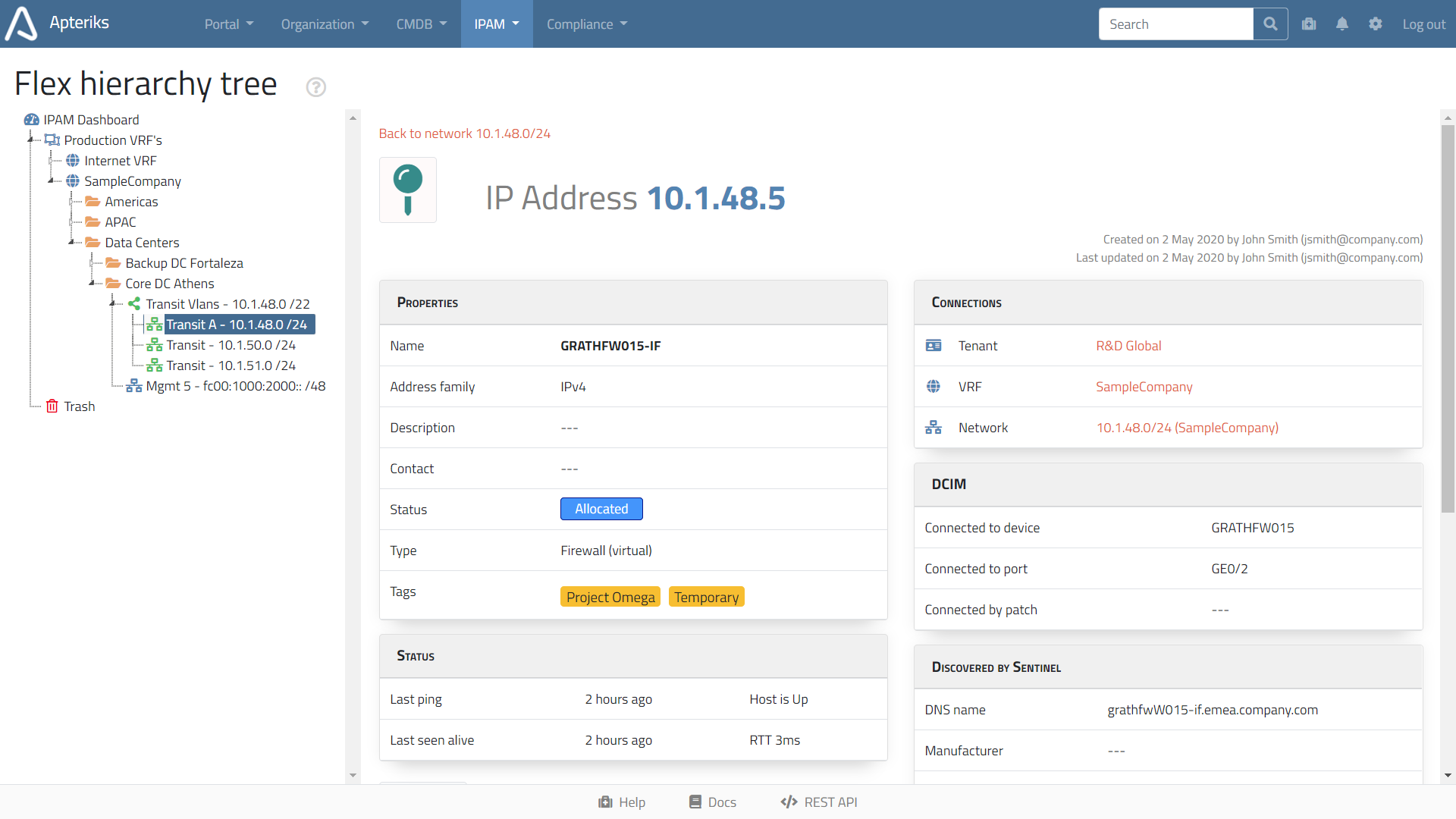
If you want to scan networks and automatically populate IPAM database, install a single copy of our tiny Sentinel agent software. It transparently integrates with your account and performs all network scanning for you.
- Discovery or IP addresses, RTT, reverse DNS names.
- Discovery of running TCP services. You can easily detect "forgotten" databases or file shares.
- Discovery of a device behind IP address by SNMP protocol: Vendor, Model, Serial number, and more.
Easy import and export
We offer simple and powerful import and export engine that covers all IPAM and CMDB objects.
- Import from CSV files. IPAM VRFs, Networks and IP addresses, or any other object types,- can be easily imported from a CSV file and exported back.
- Import from configuration files. A list of IP networks can be extracted from saved configuration files.
- Import from a routing table. A list of IP networks can be imported from a routing table of a live router.
Flexible data model
Any object can be assigned one or more tags (labels). Any object type can be expanded with custom fields.
- Custom fields can be textual or numeric, drop-down lists or checkboxes.
- Tags are universal markers that can be given to any object; clicking on a given tag displays a list of all objects with that tag.
Granular user access rights
You have full control of privileges assigned to Roles and Users
We support a powerful Role Based Access Control (RBAC) that governs privileges per Role, per object type. You can also assign privileges specific to a certain IPAM VRF or CMDB Site.
Remote integration by REST API
You can integrate your systems with our database, remotely
Do you have a BI tool, or other database, or simply want to process your data by a script?
This is all possible by the integration using REST API.